smart card multi factor authentication article We carried out systematic usability tests, designed suitable performance metrics for assessing authentication usability on an initial cohort of 100 individuals, and performed a comparative analysis of the FingerPIN scheme against traditional sequential multi-factor authentication schemes. I'm looking for some guidance on how to emulate a Mifare Classic NFC card on an Android device. Specifically, I'm interested in emulating sector 0, block 0 (UID) of the card. I have .
0 · vsc for smart card db
1 · virtual smart card windows 11
2 · virtual smart card windows 10
3 · virtual smart card rdp
4 · tpm virtual smart card management
5 · smart card invalid signature
6 · smart card for bitlocker
7 · smart card 2 factor authentication
What is TagMo: TagMo Android app for which allows cloning Amiibos using blank NTAG215 NFC tags. It was created as a result of the "DIY Amiibo cards" thread and all the collaboration that took place in it. How does it .
Multi-factor authentication (MFA) is an identity verification method in which a user must supply at least 2 pieces of evidence, such as their password and a temporary passcode, to prove their identity.
We carried out systematic usability tests, designed suitable performance metrics for assessing authentication usability on an initial cohort of 100 individuals, and performed a .
This work sheds light on the evolution of authentication systems towards Multi-Factor Authentication (MFA) starting from Single-Factor Authentication (SFA) and through Two . Multi-factor authentication (MFA) is an identity verification method in which a user must supply at least 2 pieces of evidence, such as their password and a temporary passcode, to prove their identity. We carried out systematic usability tests, designed suitable performance metrics for assessing authentication usability on an initial cohort of 100 individuals, and performed a comparative analysis of the FingerPIN scheme against traditional sequential multi-factor authentication schemes. There are two types of multi-factor authentication: 2-factor authentication and 3-factor authentication. 3-factor authentication is more secure than 2-factor authentication. In TMIS, the user generally contacts a doctor if the user has a disease or a medical condition.
vsc for smart card db
This work sheds light on the evolution of authentication systems towards Multi-Factor Authentication (MFA) starting from Single-Factor Authentication (SFA) and through Two-Factor.
In this article, we proposed a two-factor mutual authentication scheme utilizing smart cards and HECC. This new scheme utilized the finest characteristics of HECC, including compact parameters and key sizes, to enhance the real-time performance of an IoT-based TMIS system.Multi-factor authentication (MFA) is a layered approach to securing physical and logical access where a system requires a user to present a combination of two or more different authenticators to verify a user’s identity for login.
Multi-factor authentication methods found in literature. The combination of text passwords and smart cards (ID-Based) is by far the one with most number of articles, with a total of 188 (69.4%) of the articles combining the knowledge and possession factors. It is essential to protect sensitive health data and user information from malicious attacks. In the past few years, a host of multi-factor authentication schemes are proposed for e-health. However, most of them are revealed to have security flaws.
virtual smart card windows 11
Introduction. Multi-factor authentication is one of the most effective controls an organisation can implement to prevent malicious actors from gaining access to internet-facing services, systems or important data repositories and accessing sensitive data.
-ARTICLE. Advanced NFC reader technology allows organizations from several markets to benefit from strong authentication, as well as meet security and regulatory compliance requirements that mandate two-factor user authentication for accessing workstations and . Multi-factor authentication (MFA) is an identity verification method in which a user must supply at least 2 pieces of evidence, such as their password and a temporary passcode, to prove their identity. We carried out systematic usability tests, designed suitable performance metrics for assessing authentication usability on an initial cohort of 100 individuals, and performed a comparative analysis of the FingerPIN scheme against traditional sequential multi-factor authentication schemes. There are two types of multi-factor authentication: 2-factor authentication and 3-factor authentication. 3-factor authentication is more secure than 2-factor authentication. In TMIS, the user generally contacts a doctor if the user has a disease or a medical condition.
virtual smart card windows 10
This work sheds light on the evolution of authentication systems towards Multi-Factor Authentication (MFA) starting from Single-Factor Authentication (SFA) and through Two-Factor.In this article, we proposed a two-factor mutual authentication scheme utilizing smart cards and HECC. This new scheme utilized the finest characteristics of HECC, including compact parameters and key sizes, to enhance the real-time performance of an IoT-based TMIS system.
Multi-factor authentication (MFA) is a layered approach to securing physical and logical access where a system requires a user to present a combination of two or more different authenticators to verify a user’s identity for login. Multi-factor authentication methods found in literature. The combination of text passwords and smart cards (ID-Based) is by far the one with most number of articles, with a total of 188 (69.4%) of the articles combining the knowledge and possession factors.
It is essential to protect sensitive health data and user information from malicious attacks. In the past few years, a host of multi-factor authentication schemes are proposed for e-health. However, most of them are revealed to have security flaws.
Introduction. Multi-factor authentication is one of the most effective controls an organisation can implement to prevent malicious actors from gaining access to internet-facing services, systems or important data repositories and accessing sensitive data.

virtual smart card rdp
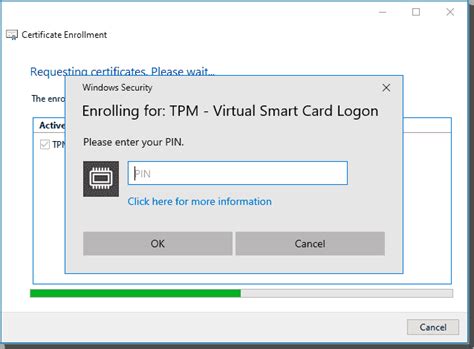
tpm virtual smart card management
smart card invalid signature
Launching alongside The Legend of Zelda: Link's Awakening for Switch, at present this cute little chap registers as a generic amiibo in Breath of the Wild and gifts generic weapons similar to the .
smart card multi factor authentication article|tpm virtual smart card management