spreading viruses via nfc tag Newly discovered Android malware steals payment card data using an infected device’s NFC reader and relays it to attackers, a novel technique that effectively clones the card so it can be used at. In the WeWork app, tap Account > Settings. 2. Tap Keycard. 3. Tap Activate > Get started. 4. Add your left and right keycard numbers in the fields provided and tap Next. 5. Stop by the Community front desk and show a valid form of .The Series 5 amiibo cards will release November 5th – the same day as the last major free update for New Horizons and the Happy Home Paradise paid DLC. See more
0 · what are nfc attacks
1 · nfc security vulnerabilities
2 · nfc security breach
3 · nfc scanning malware
4 · nfc malware download
5 · nfc cyber security
6 · nfc cyber attacks
7 · nfc attacks examples
1998 NFC wild card The Packers were three seconds away from advancing to the 1998 NFC divisional round. But three ticks of the clock was all Young and Owens needed to pull off a 30-27 victory.
Newly discovered Android malware steals payment card data using an infected device’s NFC reader and relays it to attackers, a novel technique that effectively clones the card so it can be used at.
uhf rfid clothes
Newly discovered Android malware steals payment card data using an infected device’s NFC reader and relays it to attackers, a novel technique that effectively clones the card so it can be used at. And an NFC-infected device can spread the malware to other devices it comes in contact with, leading to a massive information breach and a large-scale attack. A good way to prevent mobile malware is by only downloading apps from trusted sources. Data transmitted via NFC could potentially be altered or manipulated by an attacker. For instance, an NFC tag’s information could be modified to mislead users or to redirect them to malicious websites.

what are nfc attacks
This article delves into the vulnerabilities of NFC technology, explores the evolution of NFC attacks, discusses the impact on individuals and businesses, and provides proactive measures and advanced protection strategies to safeguard your devices. Phone malware. A malware download could be triggered by manipulating NFC signals. In 2019, a vulnerability was found in some Android devices that could let someone using NFC to prompt an Android device to download an application, provided the victim had NFC on the phone they were carrying.
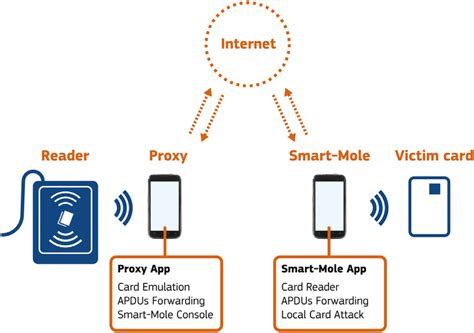
ESET Research uncovers Android malware that relays NFC data from victims’ payment cards, via victims’ mobile phones, to the device of a perpetrator waiting at an ATM. Have you heard about or experienced an NFC-related scheme or fraud? You can help spread awareness and protect others when you report it to BBB Scam Tracker. For more information In particular, contactless cloning and a relay attack are two serious risks associated with NFC. Contactless cloning is when a malware-infected device intercepts data from an NFC transaction between two devices, allowing the malicious party to steal the victim’s credentials and use them for nefarious purposes. The app is NGate, the malware that can capture NFC data from payment cards close to the infected device, and then send it to the attackers, either directly, or via a proxy. It does so through.
nfc security vulnerabilities
nfc security breach
Some hackers can carry out an ATM hack through NFC if they wave a phone through certain contactless ATMs to make them disperse money. The technique is called a "jackpotting hack." Jackpotting is usually done by accessing .

Newly discovered Android malware steals payment card data using an infected device’s NFC reader and relays it to attackers, a novel technique that effectively clones the card so it can be used at.
And an NFC-infected device can spread the malware to other devices it comes in contact with, leading to a massive information breach and a large-scale attack. A good way to prevent mobile malware is by only downloading apps from trusted sources.
Data transmitted via NFC could potentially be altered or manipulated by an attacker. For instance, an NFC tag’s information could be modified to mislead users or to redirect them to malicious websites.This article delves into the vulnerabilities of NFC technology, explores the evolution of NFC attacks, discusses the impact on individuals and businesses, and provides proactive measures and advanced protection strategies to safeguard your devices. Phone malware. A malware download could be triggered by manipulating NFC signals. In 2019, a vulnerability was found in some Android devices that could let someone using NFC to prompt an Android device to download an application, provided the victim had NFC on the phone they were carrying. ESET Research uncovers Android malware that relays NFC data from victims’ payment cards, via victims’ mobile phones, to the device of a perpetrator waiting at an ATM.
Have you heard about or experienced an NFC-related scheme or fraud? You can help spread awareness and protect others when you report it to BBB Scam Tracker. For more information In particular, contactless cloning and a relay attack are two serious risks associated with NFC. Contactless cloning is when a malware-infected device intercepts data from an NFC transaction between two devices, allowing the malicious party to steal the victim’s credentials and use them for nefarious purposes.
The app is NGate, the malware that can capture NFC data from payment cards close to the infected device, and then send it to the attackers, either directly, or via a proxy. It does so through.
nfc scanning malware
nfc malware download
The 1994 Detroit Lions season was the 65th season in the National Football League (NFL). The Lions finished with a 9–7 record and made their second consecutive playoff appearance as .The National Football League playoffs for the 1998 season began on January 2, 1999. The postseason tournament concluded with the Denver Broncos defeating the Atlanta Falcons in Super Bowl XXXIII, 34–19, on January 31, at Pro Player Stadium in Miami, Florida. As of 2024, this is the last playoffs which has not . See more
spreading viruses via nfc tag|nfc security vulnerabilities