rfid chips security A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID tags can be powered by a . Premium Stations. Auburn Basketball. US. Shows. Tiger Talk. Auburn, AL. Listen to Stream Auburn Basketball here on TuneIn! Listen anytime, anywhere!
0 · where are rfid chips used
1 · types of rfid chips
2 · rfid chips in humans
3 · rfid chips for sale
4 · rfid chip pros and cons
5 · rfid chip meaning
6 · rfid chip manufacturing
7 · pros and cons of rfid
Statewide coverage is the hallmark of the Auburn Sports Network's exclusive coverage of Auburn football. All home and away games are broadcast across the entire state of Alabama plus portions of .
RFID stands for radio-frequency identification. A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID . See moreSome people are concerned that attackers could use a handheld device in a crowd to read RFID information from nearby credit cards with contactless payment information embedded in them. Identity thieves could read the same information from an RFID . See moreRFID tags can replace bar codes and QR codes. A bar code can only be read if the reader can visually see the bar code. RFID tags can be read if the reader is nearby, even if a bar code . See more
pmp smart card
RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal money from your phone’s tap-to-pay app, or clone the chip and gain . A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID tags can be powered by a .
RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal money from your phone’s tap-to-pay app, or clone the chip and gain access to a system or data. RFID hackers have demonstrated how easy it is to get hold of information within RFID chips. As some chips are rewritable, hackers can even delete or replace RFID information with their own data. It's not too tricky for a hacker build his or . Join us as we unravel the intricacies of RFID technology, discover the diverse types of RFID cards and their vulnerabilities, explore common attack vectors, and unveil essential best practices for establishing a robust and secure RFID infrastructure.
You probably know that the embedded computer chips found in most credit and debit cards are meant to protect you from financial fraud. But you may have also heard of a scam called RFID skimming, where a thief steals the card number from your chip-embedded card just by walking past you. RFID credit cards are considered to be as safe as EMV chip cards, and data theft concerning RFID cards is uncommon. This is because of how these cards transmit information and what information.
Implementing robust security practices is crucial for safeguarding RFID systems against potential attacks. Here are some key best practices: Encrypt RFID Data: Encrypting the data transmitted between tags and readers can protect sensitive information from unauthorized access. This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks.RFID (radio frequency identification) is a form of wireless communication that incorporates the use of electromagnetic or electrostatic coupling in the radio frequency portion of the electromagnetic spectrum to uniquely identify an object, animal or person. This bulletin provides an overview of RFID technologies and recommends practices for initiating, designing, implementing, and operating RFID systems in a manner that mitigates security and privacy risks.
A small chip -- known as an RFID tag -- is attached to or implanted in an object. The tags contain information that can be read at short range via radio waves. The chip and reader don't have to touch. Some RFID tags can be powered by a . RFID chips are a convenient way to store and access data, but they can also be vulnerable to malicious attacks. Hackers can use RFID scanners to steal money from your phone’s tap-to-pay app, or clone the chip and gain access to a system or data.
RFID hackers have demonstrated how easy it is to get hold of information within RFID chips. As some chips are rewritable, hackers can even delete or replace RFID information with their own data. It's not too tricky for a hacker build his or .
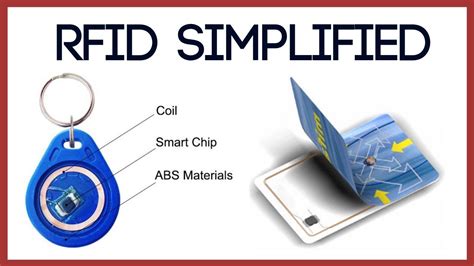
Join us as we unravel the intricacies of RFID technology, discover the diverse types of RFID cards and their vulnerabilities, explore common attack vectors, and unveil essential best practices for establishing a robust and secure RFID infrastructure. You probably know that the embedded computer chips found in most credit and debit cards are meant to protect you from financial fraud. But you may have also heard of a scam called RFID skimming, where a thief steals the card number from your chip-embedded card just by walking past you. RFID credit cards are considered to be as safe as EMV chip cards, and data theft concerning RFID cards is uncommon. This is because of how these cards transmit information and what information.
Implementing robust security practices is crucial for safeguarding RFID systems against potential attacks. Here are some key best practices: Encrypt RFID Data: Encrypting the data transmitted between tags and readers can protect sensitive information from unauthorized access. This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks. It provides practical, real-world advice on how to initiate, design, implement and operate RFID systems in a manner that mitigates security and privacy risks.RFID (radio frequency identification) is a form of wireless communication that incorporates the use of electromagnetic or electrostatic coupling in the radio frequency portion of the electromagnetic spectrum to uniquely identify an object, animal or person.
where are rfid chips used
After looking at the website for this service, the NFC SIM is only for Android, but .Philadelphia Eagles (11-5) at Dallas Cowboys (11-5)January 9, 2010Line: Dallas -3.5Over/Under: 46Starting QBs: Donovan McNabb (Phi), Tony Romo (Dal)Network: .
rfid chips security|rfid chip manufacturing