smart card based password authentication protocol smart card–based password authentication scheme becomes one of the most .
Get the best deals for nfc sdcard at eBay.com. We have a great online selection at the lowest .
0 · what is smart card authentication
1 · smart card two factor authentication
2 · smart card certificate authentication
3 · smart card based identification system
4 · smart card authentication step by
5 · smart card authentication process
6 · configure smart card authentication
7 · authenticate using your smart card
You can browse all the Animal Crossing series amiibo cards and amiibo figures, or use the filter to find specific characters. You can use My Collection to keep track of the amiibo you already own and My Wish List to make note of those .Raymond Animal Crossing Amiibo. Fast Ship from United States. All orders will be shipped in 1 .
what is smart card authentication
In this paper, we show that the improved smart card authentication scheme .
smart card two factor authentication
Section 3 presents our new efficient strong smart card based password . A robust elgamal-based password-authentication protocol using smart card for .
In this paper, we proposed an efficient robust smart card and remote client . In this article, advanced and secure smart card based authentication protocol . smart card–based password authentication scheme becomes one of the most .
Smart card-based key authentication protocols have formed the normal in the latest years, .
We also present a new efficient strong smart card based password authentication protocol that satisfies not only the minimum conditions but also advanced requirements like efficiency and mutual authentication. In this paper, we show that the improved smart card authentication scheme proposed by Xu-Zhu-Feng is vulnerable to internal and impersonation attacks. We propose an improvement of their solution, present a new efficient strong smart card authentication protocol, and demonstrate that the new protocol satisfies the requirements of strong smart .
smart card certificate authentication
smart card based identification system
smart card structure
Section 3 presents our new efficient strong smart card based password authentication protocol. Section 4 analyzes the security of the new authentication protocol. Section 5 compares the performance of the new protocol with Xu–Zhu–Feng's scheme and Lee–Chiu's scheme.
A robust elgamal-based password-authentication protocol using smart card for client-server communication. Robust multi-factor authentication for fragile communications. Targeted online password guessing: an underestimated threat. Dynamic id-based remote user password authentication schemes using smart cards: a review.
In this paper, we proposed an efficient robust smart card and remote client password-based authentication protocol based on extended chaotic maps under smart city environment using IoT, where the client can get relieve from different attacks. In this article, advanced and secure smart card based authentication protocol using elliptic curve cryptography (ECC) is proposed.
smart card–based password authentication scheme becomes one of the most common or convenient mechanisms to ensure the security of network in 2-factor.Smart card-based key authentication protocols have formed the normal in the latest years, featuring their exceptionally lightweight, easy-to-use equipment and low-cost apps. We proposed an efficient robust authentication protocol using the extended chaotic map in this article.
With its simplicity and feasibility, password-based remote user authentication becomes a popular way to control remote access to network. These years, numerous password-based authentication schemes have been proposed.The Smart Card Alliance is a not-for-profit, multi-industry association working to stimulate the understanding, adoption, use and widespread application of smart card technology. We also present a new efficient strong smart card based password authentication protocol that satisfies not only the minimum conditions but also advanced requirements like efficiency and mutual authentication.
In this paper, we show that the improved smart card authentication scheme proposed by Xu-Zhu-Feng is vulnerable to internal and impersonation attacks. We propose an improvement of their solution, present a new efficient strong smart card authentication protocol, and demonstrate that the new protocol satisfies the requirements of strong smart . Section 3 presents our new efficient strong smart card based password authentication protocol. Section 4 analyzes the security of the new authentication protocol. Section 5 compares the performance of the new protocol with Xu–Zhu–Feng's scheme and Lee–Chiu's scheme. A robust elgamal-based password-authentication protocol using smart card for client-server communication. Robust multi-factor authentication for fragile communications. Targeted online password guessing: an underestimated threat. Dynamic id-based remote user password authentication schemes using smart cards: a review.
In this paper, we proposed an efficient robust smart card and remote client password-based authentication protocol based on extended chaotic maps under smart city environment using IoT, where the client can get relieve from different attacks. In this article, advanced and secure smart card based authentication protocol using elliptic curve cryptography (ECC) is proposed. smart card–based password authentication scheme becomes one of the most common or convenient mechanisms to ensure the security of network in 2-factor.
Smart card-based key authentication protocols have formed the normal in the latest years, featuring their exceptionally lightweight, easy-to-use equipment and low-cost apps. We proposed an efficient robust authentication protocol using the extended chaotic map in this article.
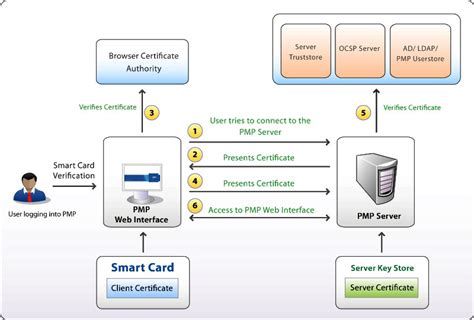
With its simplicity and feasibility, password-based remote user authentication becomes a popular way to control remote access to network. These years, numerous password-based authentication schemes have been proposed.
smart card authentication step by
smart card authentication process
Probably the most significant feature of the iPhone 6 and iPhone 6 Plus, Apple Pay allows you to use your phone to pay for goods and services in .7. Some GSM operators are using "NFC SIM" term to refer to a SIM card with an additional financial application. Such a card in combination with a NFC phone can be used for contactless payments. There are different options: it can act as a pre-paid debit card. your .
smart card based password authentication protocol|smart card certificate authentication