biometric authentication vs smart cards Biometric authentication is a security process that compares a person’s characteristics to a stored set of biometric data in order to grant access to buildings, applications, systems, and more.
Mar 23, 2022. #5. BigBlur said: Apple Pay is basically just an umbrella term for Apple's payment method. It doesn't always mean contactless payment via NFC. There may be an NFC chip, but that still doesn't mean you can do NFC/contactless stuff. This article says there is a NFC controller in the Touch Bar.QUICK ANSWER. NFC tags and readers communicate wirelessly with each other over very short distances. Tags store a small amount of data .
0 · what is biometric authentication
1 · types of biometric identification
2 · pros and cons of biometrics
3 · okta biometric authentication
4 · mfa vs biometrics
5 · is biometric authentication expensive
6 · examples of biometric authentication
7 · are biometrics real
Enable Smart Card access on your Chromebook. . SafeNet eToken .The flags are responsible for defining the NFC classes the NFC reader should detect. If you e.g. delete the line NfcAdapter.FLAG_READER_NFC_A your app will not detect any NFC tags using the NfcA technology.. The last flag NfcAdapter.FLAG_READER_NO_PLATFORM_SOUNDS .
bracelet uhf rfid tag
Hoping for a passwordless future? Multifactor authentication using biometrics may be the answer. Consider the pros, cons and implications of biometric authentication before deploying.Using smart cards with biometrics results in a trusted credential for authenticating an .
Hoping for a passwordless future? Multifactor authentication using biometrics may be the answer. Consider the pros, cons and implications of biometric authentication before deploying.Using smart cards with biometrics results in a trusted credential for authenticating an individual’s identity using one-to-one biometric verification. With the biometric template stored on the smart card, comparison can be made locally, without the need for .In this article we explore how smart cards and biometrics can work together for enhanced security, privacy and performance. Security requirements. Smart cards are both secure and portable. Additionally, they can securely store data.Biometric authentication is a security process that compares a person’s characteristics to a stored set of biometric data in order to grant access to buildings, applications, systems, and more.
brucellosis rfid tags
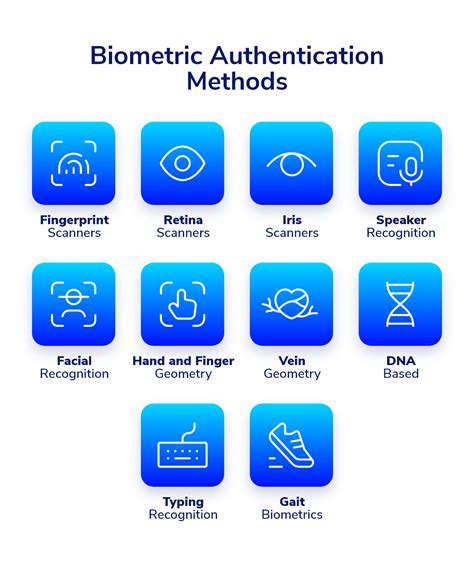
Biometric authentication is defined as a security measure that matches the biometric features of a user looking to access a device or a system. Access to the system is granted only when the parameters match those stored in the database for that particular user. In this article, we will explain the difference between FIDO2 and smartcard authentication and discuss the benefits and potential drawbacks of each. Difference between Passwordless Authentication Methods: FIDO2, SmartCard, Passwordless Phone Auth - YouTube. Difference between Passwordless Authentication Methods: FIDO2, SmartCard, Passwordless .This is done for the purpose of performing trusted communications between parties for computing and telecommunications applications. In this paper, we differentiate between machine-by-ma-chine authentication (or simply machine authentication) and human-by-machine authentication (user authentication) (see Fig. 1). Something you have (Keyfob token, key, debit card, smartcard, mobile phone); or Something you are (biometric data, such as fingerprint, retina, iris, face, veins, DNA, voiceprint, hand, typical usage patterns)
This chapter discusses the technologies of biometrics and (RFID-enabled) smart cards and their use in electronic passports, and reflects on the introduction of e-passports, and the surrounding issues regarding security and the shift in the balance of power between citizen and government. Learn how 1Kosmos enhances smart card authentication with BlockID, offering biometric-based security, identity proofing, privacy by design, distributed ledger technology, interoperability, and industry certifications.
Hoping for a passwordless future? Multifactor authentication using biometrics may be the answer. Consider the pros, cons and implications of biometric authentication before deploying.Using smart cards with biometrics results in a trusted credential for authenticating an individual’s identity using one-to-one biometric verification. With the biometric template stored on the smart card, comparison can be made locally, without the need for .In this article we explore how smart cards and biometrics can work together for enhanced security, privacy and performance. Security requirements. Smart cards are both secure and portable. Additionally, they can securely store data.Biometric authentication is a security process that compares a person’s characteristics to a stored set of biometric data in order to grant access to buildings, applications, systems, and more.
Biometric authentication is defined as a security measure that matches the biometric features of a user looking to access a device or a system. Access to the system is granted only when the parameters match those stored in the database for that particular user. In this article, we will explain the difference between FIDO2 and smartcard authentication and discuss the benefits and potential drawbacks of each. Difference between Passwordless Authentication Methods: FIDO2, SmartCard, Passwordless Phone Auth - YouTube. Difference between Passwordless Authentication Methods: FIDO2, SmartCard, Passwordless .
This is done for the purpose of performing trusted communications between parties for computing and telecommunications applications. In this paper, we differentiate between machine-by-ma-chine authentication (or simply machine authentication) and human-by-machine authentication (user authentication) (see Fig. 1).
Something you have (Keyfob token, key, debit card, smartcard, mobile phone); or Something you are (biometric data, such as fingerprint, retina, iris, face, veins, DNA, voiceprint, hand, typical usage patterns) This chapter discusses the technologies of biometrics and (RFID-enabled) smart cards and their use in electronic passports, and reflects on the introduction of e-passports, and the surrounding issues regarding security and the shift in the balance of power between citizen and government.
what is biometric authentication
types of biometric identification
pros and cons of biometrics
Long story short, been at a store for battery replacement of my Samsung S7 edge, then NFC is not working since. I've been back at the store and the guy put the phone on a wireless charger .
biometric authentication vs smart cards|examples of biometric authentication