how to use a access control rfid tag A complete RFID access control system typically consists of three main components: RFID tags, readers and writers, and management software. Users attach RFID tags as identification devices, while readers and writers send and receive signals to read tag information. Because to simulate a card, the NFC Card Emulator needs to write the Card-ID to the NFC configuration file on your phone, which requires root privileges.) ==Instructions== 1. Turn on NFC. 2. Open the NFC Card Emulator. 3. Put the NFC card on the back of the phone. After the identification is successful, enter a card name and save it. 4.
0 · rfid gate access control systems
1 · rfid based door access control
2 · rfid access control wiring diagram
3 · rfid access control system price
4 · rfid access control system pdf
5 · rfid access control manual pdf
6 · rfid access control manual
7 · rfid access control instructions
Specifications. Tap And Rate! ⭐. Zappycards uses the latest NFC technology, used in Apple Pay and Google Pay, to make reviews happen with just a tap of your phone. It's like magic to get reviews! Step 1: Simply tap the phone on the .
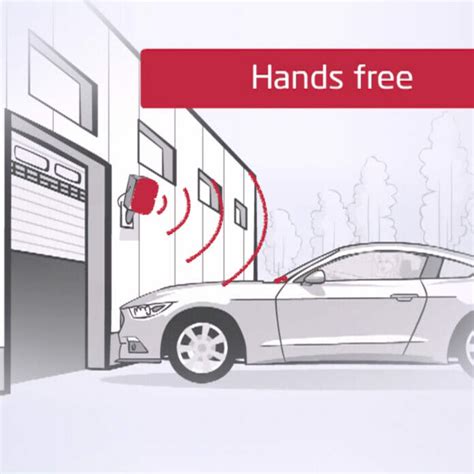
A complete RFID access control system typically consists of three main components: RFID tags, readers and writers, and management software. Users attach RFID tags as identification devices, while readers and writers send and receive signals to read tag information.A complete RFID access control system typically consists of three main components: RFID tags, readers and writers, and management software. Users attach RFID tags as identification devices, while readers and writers send and receive signals to read tag information. In this blog post, we will explore what RFID access control is, how it works, its advantages and disadvantages, and the benefits of using mobile access control system compared to systems like RFID card access. In this Nortech guide, you'll learn: What RFID access control is and the technology that underpins it. How RFID access control works. The benefits of using RFID access control. Which industries can benefit most from RFID access control. table of contents.
When an access control card (the RFID tag) is shown to the access control reader next to the door (the RFID reader with RFID antenna), that specific number is sent to the access control panel (a physical controller).

RFID access control systems work by utilizing a series of tags, readers and computer servers to grant door access to any authorized individuals in possession of valid credentials.RFID access control uses a system of tags, readers, and computer servers to allow access to verified users. The pros of RFID entry systems are ease of use, easy replacement, and practicality for doors, gates, vehicles, and elevators.
Step 1: Components of the System. As already mentioned earlier, the RFID access control system consists of the following components: RFID tags, antennas, an RFID reader, and a transceiver. The RFID tags are attached to key cards or . An RFID door lock system is an automated access control system that uses radio frequency identification (RFID) technology to identify and authenticate users. It works by using a wireless signal from an RFID tag, keyfob, or card to unlock doors, gates, and other entry points. RFID access control system allows determines who enters or leaves specific premises at any given time. It includes an automated system that identifies an individual, authenticates their details, and allows access upon verification. Key Takeaways. RFID access control uses RFID technology to verify a resident’s credentials. RFID access control uses a system of tags, readers, and computer servers to allow access to verified users. The pros of RFID entry systems are ease of use, easy replacement, and practicality for doors, gates, vehicles, and elevators.
rfid gate access control systems
A complete RFID access control system typically consists of three main components: RFID tags, readers and writers, and management software. Users attach RFID tags as identification devices, while readers and writers send and receive signals to read tag information. In this blog post, we will explore what RFID access control is, how it works, its advantages and disadvantages, and the benefits of using mobile access control system compared to systems like RFID card access. In this Nortech guide, you'll learn: What RFID access control is and the technology that underpins it. How RFID access control works. The benefits of using RFID access control. Which industries can benefit most from RFID access control. table of contents.
When an access control card (the RFID tag) is shown to the access control reader next to the door (the RFID reader with RFID antenna), that specific number is sent to the access control panel (a physical controller).RFID access control systems work by utilizing a series of tags, readers and computer servers to grant door access to any authorized individuals in possession of valid credentials.RFID access control uses a system of tags, readers, and computer servers to allow access to verified users. The pros of RFID entry systems are ease of use, easy replacement, and practicality for doors, gates, vehicles, and elevators. Step 1: Components of the System. As already mentioned earlier, the RFID access control system consists of the following components: RFID tags, antennas, an RFID reader, and a transceiver. The RFID tags are attached to key cards or .
An RFID door lock system is an automated access control system that uses radio frequency identification (RFID) technology to identify and authenticate users. It works by using a wireless signal from an RFID tag, keyfob, or card to unlock doors, gates, and other entry points.
RFID access control system allows determines who enters or leaves specific premises at any given time. It includes an automated system that identifies an individual, authenticates their details, and allows access upon verification.
anti theft rfid tag
allflex rfid tags
rfid based door access control
rfid access control wiring diagram
About this item. NFC Forum Specifications. ISO/IEC 14443. Compatible with RC-S380/S: Can be used in applications developed for the RC-S380/S. › See .Read/Write capability with FeliCa card / FeliCa-compatible devices and ISO/IEC 14443 Type A / Type B cards. See more
how to use a access control rfid tag|rfid based door access control