encryption in smart cards As a National eID card, smart health card, residence permit, or electronic passport, smart card technology offers more robust identification and authentication tools for both authorities' and citizens' benefits. Specifications. iPad 3 (Wi-Fi + Cellular) A1403 @Apple. Tablet 1 GB RAM, 64 GB max storage, .
0 · Virtual Smart Card Overview
1 · Understanding and Evaluating Virtual S
2 · About Smart Cards : Frequently Asked Questions
3 · About Smart Cards : Frequently Asked
Yes, this is technically possible. The figures are Mifare Ultralight NFC tags, and the data is readable without any keys. Writing is locked, however. Most NFC enabled Android .Here, Hunter Cat NFC communicates with a passive tag, NFC smart card, or an NFC device operating in card emulation mode. It can read or write to a tag (although reading is a more common use-case because tags will often be .
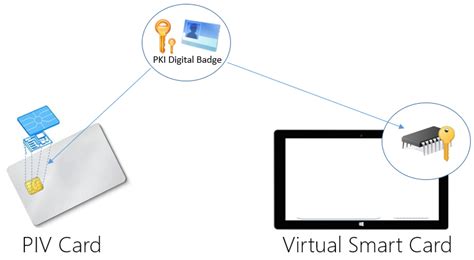
Virtual Smart Card Overview
Encryption. Smart card technology can provide a robust set of encryption capabilities including key generation, secure key storage, hashing, and digital signing. These capabilities can be . By utilizing TPM devices that provide the same cryptographic capabilities as conventional smart cards, virtual smart cards accomplish the three key properties that are desired for smart cards: nonexportability, isolated cryptography, and anti-hammering.Encryption. Smart card technology can provide a robust set of encryption capabilities including key generation, secure key storage, hashing, and digital signing. These capabilities can be used by a system to protect privacy in a number of ways.
Successful attacks against smart cards have included power glitching; differential power analysis; and capping them then using an ion-beam microscope to read out the key bits from the flash memory. Because the cards are always at risk of being stolen by an advanced attacker, each card is usually issued a unique key.As a National eID card, smart health card, residence permit, or electronic passport, smart card technology offers more robust identification and authentication tools for both authorities' and citizens' benefits.
rfid chip and the mark of the beast
In this paper we are going to describe the most popular and efficient encryption algorithms in smart cards such as RSA, ECC, DES and ECDSA and comparisons between these algorithms to find out the differences. This result can be helpful for such new device such as multipurpose smart cards. Virtual smart cards can be used for authentication to external resources, protection of data by encryption, and integrity through signing. You can deploy virtual smart cards by using in-house methods or a purchased solution, and they can be a replacement for other methods of strong authentication in a corporate setting of any scale.
Smart cards are widely used to encrypt digital television streams. VideoGuard is a specific example of how smart card security worked.Smart Card Authentication. Offering a range of certificate-based PKI smart cards with strong multi-factor authentication. Our Smart card authentication meets the highest security standards!Choose the right type of smart card for your application by evaluating cost versus functionality and determine your required level of security. The following chart demonstrates the general rules of thumb.
Summary. Another science – some would say art – that is very important to smart cards is cryptography. Cryptography is an essential part of many of the security functions for which smart cards are used. By utilizing TPM devices that provide the same cryptographic capabilities as conventional smart cards, virtual smart cards accomplish the three key properties that are desired for smart cards: nonexportability, isolated cryptography, and anti-hammering.Encryption. Smart card technology can provide a robust set of encryption capabilities including key generation, secure key storage, hashing, and digital signing. These capabilities can be used by a system to protect privacy in a number of ways. Successful attacks against smart cards have included power glitching; differential power analysis; and capping them then using an ion-beam microscope to read out the key bits from the flash memory. Because the cards are always at risk of being stolen by an advanced attacker, each card is usually issued a unique key.
As a National eID card, smart health card, residence permit, or electronic passport, smart card technology offers more robust identification and authentication tools for both authorities' and citizens' benefits.
In this paper we are going to describe the most popular and efficient encryption algorithms in smart cards such as RSA, ECC, DES and ECDSA and comparisons between these algorithms to find out the differences. This result can be helpful for such new device such as multipurpose smart cards. Virtual smart cards can be used for authentication to external resources, protection of data by encryption, and integrity through signing. You can deploy virtual smart cards by using in-house methods or a purchased solution, and they can be a replacement for other methods of strong authentication in a corporate setting of any scale.Smart cards are widely used to encrypt digital television streams. VideoGuard is a specific example of how smart card security worked.Smart Card Authentication. Offering a range of certificate-based PKI smart cards with strong multi-factor authentication. Our Smart card authentication meets the highest security standards!
Choose the right type of smart card for your application by evaluating cost versus functionality and determine your required level of security. The following chart demonstrates the general rules of thumb.
Understanding and Evaluating Virtual S
About Smart Cards : Frequently Asked Questions
rfid chip mark of the beast
2. Download an NFC-enabled access control app. There are many different apps available, but we recommend DuplicateCard.com. 3. Place your .
encryption in smart cards|Virtual Smart Card Overview