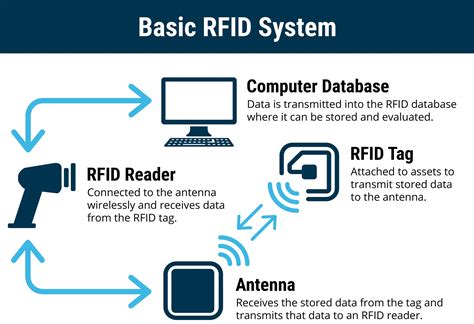
authorization of readers in rfid The concept. As you may know a few things are needed to have an operational RFID system in place: A reader, that is connected to (or integrated with) An antenna, that sends out a radio signal. A tag (or transponder) that returns the signal with information added.
$36.47
0 · rfid tags and readers
1 · rfid readers definition
2 · rfid reader access control
3 · rfid card reader system
4 · rfid authentication
5 · rfid access card reader
6 · access rfid tags and readers
7 · access rfid code reader
While the NFC reader/writer is reading/writing data, power requirements temporarily increase, .
rfid tags and readers
RFID-powered authentication gives users easy access to business systems they need — and nothing they don’t — with a single, simple credential. Connected Workplace. Access Everywhere. Benefits of RFID-Enabled Authentication. Secure. Prevents unauthorized physical and digital .HOW RFID AUTHENTICATION AND ACCESS CONTROL WORKS IN INDUSTRIAL .
RFID-powered authentication gives users easy access to business systems they need — and nothing they don’t — with a single, simple credential. Connected Workplace. Access Everywhere. Benefits of RFID-Enabled Authentication. Secure. Prevents unauthorized physical and digital access. Efficient.
high frequency rfid card
HOW RFID AUTHENTICATION AND ACCESS CONTROL WORKS IN INDUSTRIAL AUTOMATION APPLICATIONS. An RFID-based authentication and access control system has cards, readers, and a plant network con-nection to an HMI, PLC or robot controller. There is also a network connection to the plant wide IT data servers.A complete RFID access control system typically consists of three main components: RFID tags, readers and writers, and management software. Users attach RFID tags as identification devices, while readers and writers send and receive signals to read tag information. The concept. As you may know a few things are needed to have an operational RFID system in place: A reader, that is connected to (or integrated with) An antenna, that sends out a radio signal. A tag (or transponder) that returns the signal with information added. Radio frequency identification (RFID) enables you to read data encoded in RFID chips using specialized equipment—RFID readers. Unlike RFID, near-field communication, or NFC, is a two-way channel for transferring data between devices like phones and smartwatches.
Unauthorized reading of RFID tags presents a risk to privacy and to business secrecy. [132] Unauthorized readers can potentially use RFID information to identify or track packages, persons, carriers, or the contents of a package. [ 130 ] RFID reader: This device reads the information stored on the RFID tags and sends it to the access control system to allow authorization. When someone presents their RFID card, ID badge, or key fob to an RFID-enabled door, the reader initiates a signal to the tag. Next, the tag transmits its distinct identifying information to the reader.
RFID readers can be used throughout an organizational ecosystem for multipurpose authentication with existing employee building-entry ID cards, adding functionality like time-based access control, access to manufacturing processes and hazardous areas. RFID is a wireless technology that uses electromagnetic fields to identify and track objects, such as vehicles, by reading data stored on a tag attached to the object. Every RFID system consists of three main components: Reader: A .
How do RFID readers authenticate and encrypt the communication with RFID tags? Powered by AI and the LinkedIn community. 1. Authentication protocols. 2. Encryption schemes. Be the first to.RFID-powered authentication gives users easy access to business systems they need — and nothing they don’t — with a single, simple credential. Connected Workplace. Access Everywhere. Benefits of RFID-Enabled Authentication. Secure. Prevents unauthorized physical and digital access. Efficient.HOW RFID AUTHENTICATION AND ACCESS CONTROL WORKS IN INDUSTRIAL AUTOMATION APPLICATIONS. An RFID-based authentication and access control system has cards, readers, and a plant network con-nection to an HMI, PLC or robot controller. There is also a network connection to the plant wide IT data servers.A complete RFID access control system typically consists of three main components: RFID tags, readers and writers, and management software. Users attach RFID tags as identification devices, while readers and writers send and receive signals to read tag information.
The concept. As you may know a few things are needed to have an operational RFID system in place: A reader, that is connected to (or integrated with) An antenna, that sends out a radio signal. A tag (or transponder) that returns the signal with information added. Radio frequency identification (RFID) enables you to read data encoded in RFID chips using specialized equipment—RFID readers. Unlike RFID, near-field communication, or NFC, is a two-way channel for transferring data between devices like phones and smartwatches.
Unauthorized reading of RFID tags presents a risk to privacy and to business secrecy. [132] Unauthorized readers can potentially use RFID information to identify or track packages, persons, carriers, or the contents of a package. [ 130 ]
RFID reader: This device reads the information stored on the RFID tags and sends it to the access control system to allow authorization. When someone presents their RFID card, ID badge, or key fob to an RFID-enabled door, the reader initiates a signal to the tag. Next, the tag transmits its distinct identifying information to the reader.
RFID readers can be used throughout an organizational ecosystem for multipurpose authentication with existing employee building-entry ID cards, adding functionality like time-based access control, access to manufacturing processes and hazardous areas. RFID is a wireless technology that uses electromagnetic fields to identify and track objects, such as vehicles, by reading data stored on a tag attached to the object. Every RFID system consists of three main components: Reader: A .

how long do passive rfid tags last
Write Phone Number To NFC Tag. Copyright © 2023 NFCToolsOnline
authorization of readers in rfid|rfid readers definition