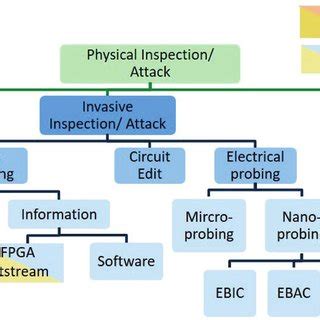
physical attacks on smart cards In the 1990s, physical attacks on smart cards adversely affected the pay-TV industry. During that period, smart cards were widely used for payment applications, and their . Touch the WRITE TAG (AUTO) button and press your NTAG215 NFC tag to your Android device. The stickers aren't re-writeable so I'd advise against trying that in the future so you don't mess the sticker up. Another ntag215 tag I recommend .
0 · Physical Inspection and Attacks: An Overview
1 · Hackers can steal cryptographic keys by video
2 · Attacking smart card systems: Theory and practice
$16.44With the advent of technology, it is now possible to copy an NFC card to your phone. This can be done with the help of Rango NFC, provided your device is rooted. To clone a card, hold the card you want to clone against your phone .
Researchers have devised a novel attack that recovers the secret encryption keys stored in smart cards and smartphones by using cameras in iPhones or commercial surveillance systems to video.
long range rfid reader raspberry pi
In the 1990s, physical attacks on smart cards adversely affected the pay-TV industry. During that period, smart cards were widely used for payment applications, and their . In this work, we analyse two well-known classes of physical attacks—fault injections and side-channel attacks—and their application to mobile devices. Such attacks are well-understood in the smart card and secure element (SE) domain (Guilley et al. 2010; Kim and Quisquater 2007; Markantonakis et al. 2009; Quisquater and Samyde 2001). Researchers have devised a novel attack that recovers the secret encryption keys stored in smart cards and smartphones by using cameras in iPhones or commercial surveillance systems to video.

Physical Inspection and Attacks: An Overview
In the 1990s, physical attacks on smart cards adversely affected the pay-TV industry. During that period, smart cards were widely used for payment applications, and their security was considered state of the art. A designer incorporating smart cards into a system should consider both attacks that apply to the security of the physical smart card token and the system as a whole. This article provides a brief overview of selected attacks on smart cards, and also examines cases where real world systems using smart cards were attacked because of factors not .
Infecting several phones an attacker could have under his control a large set of cards, a sort of “Internet of Smart Cards”. We show that surveying a decade of research and development in the contactless cards field such attacks look feasible according the current social context and the level of technology. This article examines the range of possible attacks against smart cards, and the measures that can be used to protect against these attacks.Basically, smart card attacks can be classified into three main categories: social, logical and physical attacks. Social Attacks. These are the oldest. The idea behind these attacks is to obtain information directly from the manufacturer using classical social engineering techniques.Computers are physical objects, which means they can be vulnerable to physical attacks. These attacks might involve an attacker physically interacting with the computer, or involve other physical devices like smartcards or flash drives.
Hackers can steal cryptographic keys by video
Attacking smart card systems: Theory and practice
This survey discusses smart card technology in detail and provides a comprehensive taxonomy of security attacks on smart card–based applications and their countermeasures, and covers some of the open source tools available for its development.

More recently, the idea has emerged to combine logical attacks with a physical attack, in order to evade bytecode verification. We present practical work done recently on this topic, as well as some countermeasures that can be put in place against such attacks, and how they can be evaluated by security laboratories.
In this work, we analyse two well-known classes of physical attacks—fault injections and side-channel attacks—and their application to mobile devices. Such attacks are well-understood in the smart card and secure element (SE) domain (Guilley et al. 2010; Kim and Quisquater 2007; Markantonakis et al. 2009; Quisquater and Samyde 2001).
Researchers have devised a novel attack that recovers the secret encryption keys stored in smart cards and smartphones by using cameras in iPhones or commercial surveillance systems to video. In the 1990s, physical attacks on smart cards adversely affected the pay-TV industry. During that period, smart cards were widely used for payment applications, and their security was considered state of the art. A designer incorporating smart cards into a system should consider both attacks that apply to the security of the physical smart card token and the system as a whole. This article provides a brief overview of selected attacks on smart cards, and also examines cases where real world systems using smart cards were attacked because of factors not . Infecting several phones an attacker could have under his control a large set of cards, a sort of “Internet of Smart Cards”. We show that surveying a decade of research and development in the contactless cards field such attacks look feasible according the current social context and the level of technology.
This article examines the range of possible attacks against smart cards, and the measures that can be used to protect against these attacks.Basically, smart card attacks can be classified into three main categories: social, logical and physical attacks. Social Attacks. These are the oldest. The idea behind these attacks is to obtain information directly from the manufacturer using classical social engineering techniques.
Computers are physical objects, which means they can be vulnerable to physical attacks. These attacks might involve an attacker physically interacting with the computer, or involve other physical devices like smartcards or flash drives.This survey discusses smart card technology in detail and provides a comprehensive taxonomy of security attacks on smart card–based applications and their countermeasures, and covers some of the open source tools available for its development.
While bright colors work best for plastic business cards, you’re not limited in what you can design. You could even use all white (no printing) or black on your plastic business cards. Explore VistaPrint’s plastic business cards! With templated .
physical attacks on smart cards|Attacking smart card systems: Theory and practice